:This script will create the proper domain local group and global groups
:The only input this script needs is the UNC path to the folder. At the end
:of this script the only thing you'll need to do is add the users from the actual
:folder to the global group.
:
:eg create-groups.cmd "\\file01\HR\HR Support Group\HR Team\HR Support Services"
SET /P Permissions=What permissions will this group have ([F]ULL/[M]ODIFIY/[RO]READ ONLY)?
IF /I '%PERMISSIONS%' EQU 'F' SET PERMISSIONS=FULL
IF /I '%PERMISSIONS%' EQU 'M' SET PERMISSIONS=MODIFY
IF /I '%PERMISSIONS%' EQU 'RO' SET PERMISSIONS=RO
:ECHO %1 |sed "s/\\\\//g"|sed "s/\\/\./g" | sed "s/\"//g"
:We parse the command line for the UNC structure, now we need to find the last folder
for /F "tokens=*" %%A IN ('ECHO %1 ^|sed ^"s/\\\\//g^"^|sed ^"s/\\/\./g^" ^| sed ^"s/\^"//g^"') DO set groupname=%%A
set str=%groupname%
set N=0
setLocal EnableDELAYedExpansion
:loop
if !N! equ 55 (
goto :exceedcharacterquota
)
set /A N+=1
ECHO N=!N!
if "!str:~1!" neq "" (
set str=!str:~1!
goto :loop
)
goto :skip-string-modification
:if string length exceeds 55 chars, take the first 25 chars and the last 25 chars with an ellipse (...)
:in between.
:exceedcharacterquota
set string-part-one=!groupname:~0,25!
set string-part-two=!groupname:~-25!
set GROUPNAME=!string-part-one!...!string-part-two!
:skip-string-modification
setLocal disableDELAYedExpansion
:Remove any trailing spaces
for /F "tokens=*" %%A IN ('ECHO %GROUPNAME% ^|sed ^"s/ $//g^"') DO set groupname=%%A
ECHO GROUP=%GROUPNAME%
:Sets OU to domain local resource group...
SET OUL=OU=Resource,OU=Security Groups,OU=AD Project 3,DC=CCS,DC=CORP
dsadd group "CN=F.lg.%GROUPNAME%.%PERMISSIONS%,%OUL%" -desc %1 -secgrp yes -scope l
:Sets OU to Global group...
SET OUG=OU=Global,OU=Security Groups,OU=AD Project 3,DC=CCS,DC=CORP
dsadd group "CN=gg.%GROUPNAME%.%PERMISSIONS%,%OUG%" -desc %1 -secgrp yes -scope g
:adds the global group to the domain local group
dsmod group "CN=F.lg.%GROUPNAME%.%PERMISSIONS%,%OUL%" -addmbr "CN=gg.%GROUPNAME%.%PERMISSIONS%,%OUG%"
Friday, November 18, 2011
Group Creation Script
The final script:
Count Characters in a Batch File
I have an issue where I need to ensure I don't exceed a certain number of characters in a script. Specifically, I cannot exceed 64 characters while making a group through script in AD. To do this I came up with the following:
ECHO OFF
:Set some variables, the string variable, a second string variable and our starting count.
set str=\\fileservertestserver\accounting\Budgets\Budgets 2012\2012 Budget GA Loads
set str2=%str%
set N=0
setLocal EnableDELAYedExpansion
:the loop works like so... we check to see if N has been incremented to 55 (our
:target number of characters). If it has, it goes to a new routine which creates
:our path. If it does not, we increment N by one then check to see if the string
:has reached a NULL character. If it has not reached "55" then goto loop and repeat.
:loop
if !N! equ 55 (
goto :exceedcharacterquota
)
set /A N+=1
ECHO N=!N!
if "!str:~1!" neq "" (
set str=!str:~1!
goto :loop
)
:if string length exceeds 55 chars, take the first 25 chars and the last 25 chars with an ellipse (...)
:in between.
:exceedcharacterquota
set string-part-one=!str2:~0,25!
set string-part-two=!str2:~-25!
echo !string-part-one!...!string-part-two!
Monday, November 07, 2011
Working around a VPN administrator issue...
We recently had a workstation that was sent to a user that didn't have the user in the local administrator group. This should be an easy fix, just add the user to that group. We could not though, as the user was a domain user and the computer was not on a network with a domain controller. I did have the local administrator account password and could login with it, but the VPN technology we use (Juniper's Network Connect) requires local administrator rights to install it (which I was able to do) but is setup to verify that the user account is a domain user account. Without the user account being from the domain and a local administrator account, Network Connect will not connect to our network.
Well, this is a bit of a pickle. Since this user was in Victoria BC and I was in Calgary AB, I needed to find a way to connect their computer to our domain network so they could authenticate against our DC and then I could add their account to the local admin group.
To do this I did the following:
1) Using the local administrator account on the remote computer, install TeamViewer and set it to launch on Windows Startup.
2) Setup unattended access through TeamViewer and install the VPN client on the remote computer and my local computer.
3) The network the remote computer was on was a 192.168.X.X and our network is a 10.X.X.X. So I set a persistent route on the remote computer to route all traffic to the 10/8 network to the VPN ip on *my* (the local) end "route add 10.0.0.0 mask 255.0.0.0 7.154.200.11 -p"
4) Add a DNS entry on both the Teamviewer and ethernet adapter of the remote computer to the DNS on one of the computers in the Domain (a 10.X.X.X address).
5) I downloaded and installed NAT32 onto the local computer. I configured it like so:
Teamviewer VPN Adapter - Private
Local Network Adapter - Internet
"Share the Windows IP Address"
Then NAT32 generated a screen like so:
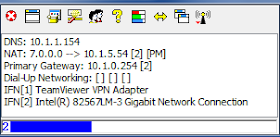
From here, I connected to the user through Teamviewer's VPN and via Remote Control. I confirmed I could ping the DNS server on the domain from the remote computer. I rebooted the computer, phoned the user and found out when it was at the CTRL-ALT-DEL screen. Once it was at that stage, I connected to it, from TeamViewer's VPN, and then I could login to the domain. While under the users account, I started an elevated command-prompt and opened compmgmt.msc and added her domain account to the local admin account. I then had her log off, and via Teamviewer's remote control, logged back on via the local admin account. I then removed the persistent static route and logged back off and had the user log back in. From here, she had all the rights she needed to launch Network Connect and Network Connect saw that this computer is connected to the domain and allowed connection.
http://kb.juniper.net/InfoCenter/index?page=content&id=KB9084
Well, this is a bit of a pickle. Since this user was in Victoria BC and I was in Calgary AB, I needed to find a way to connect their computer to our domain network so they could authenticate against our DC and then I could add their account to the local admin group.
To do this I did the following:
1) Using the local administrator account on the remote computer, install TeamViewer and set it to launch on Windows Startup.
2) Setup unattended access through TeamViewer and install the VPN client on the remote computer and my local computer.
3) The network the remote computer was on was a 192.168.X.X and our network is a 10.X.X.X. So I set a persistent route on the remote computer to route all traffic to the 10/8 network to the VPN ip on *my* (the local) end "route add 10.0.0.0 mask 255.0.0.0 7.154.200.11 -p"
4) Add a DNS entry on both the Teamviewer and ethernet adapter of the remote computer to the DNS on one of the computers in the Domain (a 10.X.X.X address).
5) I downloaded and installed NAT32 onto the local computer. I configured it like so:
Teamviewer VPN Adapter - Private
Local Network Adapter - Internet
"Share the Windows IP Address"
Then NAT32 generated a screen like so:

From here, I connected to the user through Teamviewer's VPN and via Remote Control. I confirmed I could ping the DNS server on the domain from the remote computer. I rebooted the computer, phoned the user and found out when it was at the CTRL-ALT-DEL screen. Once it was at that stage, I connected to it, from TeamViewer's VPN, and then I could login to the domain. While under the users account, I started an elevated command-prompt and opened compmgmt.msc and added her domain account to the local admin account. I then had her log off, and via Teamviewer's remote control, logged back on via the local admin account. I then removed the persistent static route and logged back off and had the user log back in. From here, she had all the rights she needed to launch Network Connect and Network Connect saw that this computer is connected to the domain and allowed connection.
http://kb.juniper.net/InfoCenter/index?page=content&id=KB9084